It is about this time of the year that many of the much
larger Cyber vendors start to publish their reports as to what transpired on the
Cyber threat landscape. Some of these
include IBM, Malware Bytes, etc. Of course,
there those other vendors that come out with their own periodically, and if
there is one that relates to a blog posting that I am writing on, I usually
cite it there.
One such vendor that comes out regularly is Verizon. One may often think of them as the wireless
business, but they are also strong in the Cyber area as well, and their reports
are fairly exhaustive in nature. So
without much ado, I now introduce to you the “2022 Data Breach Investigations
Report, once again, made available from Verizon.
Interestingly enough, Verizon did not poll any respondents
in any particular survey, but rather, they looked at the total number of security
breaches that occurred in 2021, and from there, formulated a number of hypotheses.
So for this project, there were a total of 23,896 security
incidents which were studied, and from that 5,212 were actual data breaches. From
here, these incidents and breaches were divided into eight distinct groups, which
are as follows:
*Web application attacks:
As the name implies, these are attacks against Web based
apps, no matter what they may be.
*DoS/DDoS attacks:
This is the where the server is flooded with malformed data
packets, causing to almost shut down.
*Lost/stolen assets:
These are both the digital and physical assets that have
either lost or stolen.
*Miscellaneous errors:
These are the unintentional mistakes caused most likely by
employees.
*Privilege misuse:
This is the unapproved escalation of privileges, rights, and
permissions.
*Social engineering:
This is when an individual or employee is tricked into giving
out confidential information and/or data points.
*System intrusion:
These are pretty much the Malware based attacks.
*Everything else:
This includes any other threat vectors that do not fit in
any of the above categories.
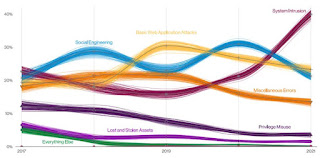
These can be seen in the illustration below:
(SOURCE: https://www.darkreading.com/edge-threat-monitor/most-common-threats-in-dbir)
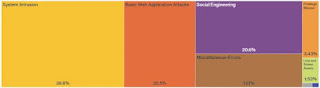
From the above, the top two security threat vectors were that
of Web applications, and Social Engineering, which is not surprising. This can be seen in the diagram below:
(SOURCE: https://www.darkreading.com/edge-threat-monitor/most-common-threats-in-dbir)
Here are some of the other key findings from the Verizon Report:
*Systems intrusions are probably amongst the most difficult to
detect, because there are so many different avenues that the Cyber attacker can
get in and stay for a very period of time going unnoticed. This is why the average time to detect a
security breach is 300 days.
*One key reason for the increase in in the system intrusion
attacks is the sheer rise in the total number of supply chain attacks that are happening
as well, such as the Solar Winds example, in which over 1,000+ victims were
impacted through one single point of failure.
It is through here that the Cyberattacker was able to deploy their malicious
payloads.
*In these kind of attacks, there has been a drastic rise in the
number of command-and-control VMs that are being used, in an attempt to avoid
being tracked down.
*For systems intrusion attacks, the most commonly used threat
vectors are as follows:
Ø
Third party software;
Ø
Software updates and patches;
Ø
Desktop sharing software packages;
Ø
E-mail, primarily that of Phishing.
*With regards to the Web based application attacks, the use
of backdoors, remote injection techniques, and the use of desktop sharing
software to compromise the hosted server were the most vectors that were
used.
*In terms of the most impacted victims, the breakdown is as
follows:
Ø
For system intrusion: Manufacturing.
Ø
For Web based apps: Manufacturing and financial services;
Ø
For Social Engineering: Retail and professional organizations (such
as staffing firms).
Finally, the report stated that in 82% of the security
breaches that were examined, the human element played a key role whether it was
intentional or not.
My Thoughts On This:
Truthfully speaking, I have not read the entire Verizon
report in detail, there are just some of the key findings that I picked up from
it. But whatever else it has mentioned,
it is true that, IMHO Web based attacks and Social Engineering are going to be
the norm of the future, going well into 2023.
This stems from two key areas:
Insecure source code that is being used to create the Web application;
and Cyberattackers are fully aware now that people’s minds are on protecting
their digital assets.
Therefore, why not turn attention to what is called as the weakest
link in the security chain, which is the human being? Social engineering attacks work great here,
especially for those people that are on the go and as a result, do not carefully
think about what they are saying. This is
well exemplified by the retail sector, as the report has found.
But another key thing to keep in mind is that with systems
intrusion, we will probably not see the likes of another Solar Winds for some
time to come. Rather, as it has been forecasted, we will probably see much
smaller scale ones happening, but the objective of the Cyberattacker here is to
cause even more mass confusion for the IT Security teams that have to deal with
them.
Finally, Phishing, probably the oldest of the threat variants
will never go away. It will be here for
a long time yet to come, with more potent variations of it coming out.
Finally, the Verizon Report can be downloaded at this link:
I am eventually planning to make an eBook based on this, so
stay tuned!!!





Thanks for sharing this blog. If you are interested in buying and selling bitcoin. Visit Binance because it is the best crypto trading platform.
ReplyDelete